| Question.6 A user calls the help desk to report that none of the files on a PC will open. The user also indicates a program on the desktop is requesting payment in exchange for file access. A technician verifies the user’s PC is infected with ransomware. Which of the following should the technician do FIRST? (A) Scan and remove the malware. (B) Schedule automated malware scans. (C) Quarantine the system. (D) Disable System Restore. |
6. Click here to View Answer
Correct Answer: C
| Question.7 A company is issuing smartphone to employees and needs to ensure data is secure if the devices are lost or stolen. Which of the following provides the BEST solution? (A) Anti-malware (B) Remote wipe (C) Locator applications (D) Screen lock |
7. Click here to View Answer
Correct Answer: B
| Question.8 A user reports seeing random, seemingly non-malicious advertisement notifications in the Windows 10 Action Center. The notifications indicate the advertisements are coming from a web browser. Which of the following is the BEST solution for a technician to implement? (A) Disable the browser from sending notifications to the Action Center. (B) Run a full antivirus scan on the computer. (C) Disable all Action Center notifications. (D) Move specific site notifications from Allowed to Block. |
8. Click here to View Answer
Correct Answer: D
| Question.9 After clicking on a link in an email, a Chief Financial Officer (CFO) received the following error: 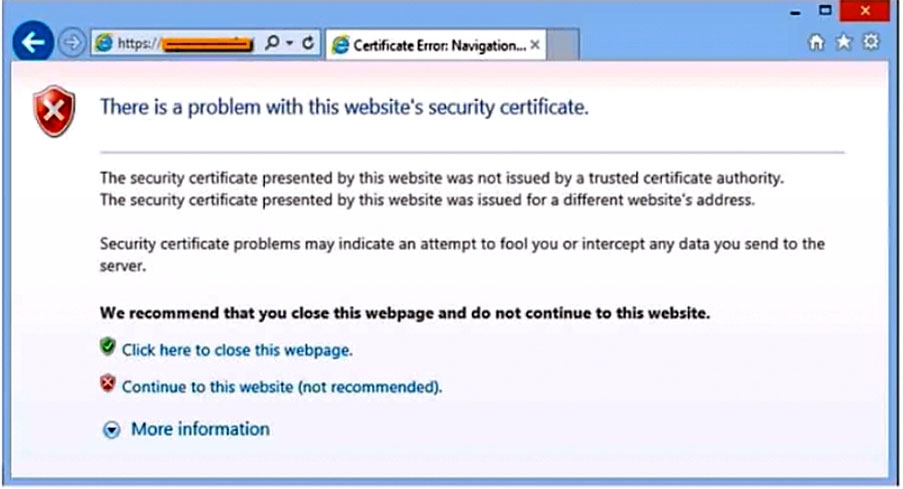 The CFO then reported the incident to a technician. The link is purportedly to the organization’s bank. Which of the following should the technician perform FIRST? A. Update the browser’s CRLs. B. File a trouble ticket with the bank. C. Contact the ISP to report the CFO’s concern. D. Instruct the CFO to exit the browser. |
9. Click here to View Answer
Correct Answer: D
| Question.10 A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus. Which of the following is the MOST effective way to check other machines on the network for this unknown threat? (A) Run a startup script that removes files by name. (B) Provide a sample to the antivirus vendor. (C) Manually check each machine. (D) Monitor outbound network traffic. |
10. Click here to View Answer
Correct Answer: C
