| Question.46 The Chief Information Security Officer is concerned about the possibility of employees downloading malicious files from the internet and opening them on corporate workstations. Which of the following solutions would be BEST to reduce this risk? (A) Integrate the web proxy with threat intelligence feeds. (B) Scan all downloads using an antivirus engine on the web proxy. (C) Block known malware sites on the web proxy. (D) Execute the files in the sandbox on the web proxy. |
46. Click here to View Answer
Answer: B
| Question.47 An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key. Which of the following would BEST secure the REST API connection to the database while preventing the use of a hard-coded string in the request string? (A) Implement a VPN for all APIs. (B) Sign the key with DSA. (C) Deploy MFA for the service accounts. (D) Utilize HMAC for the keys. |
47. Click here to View Answer
Answer: A
Reference:
https://eclipsesource.com/blogs/2016/07/06/keyed-hash-message-authentication-code-in-rest-apis/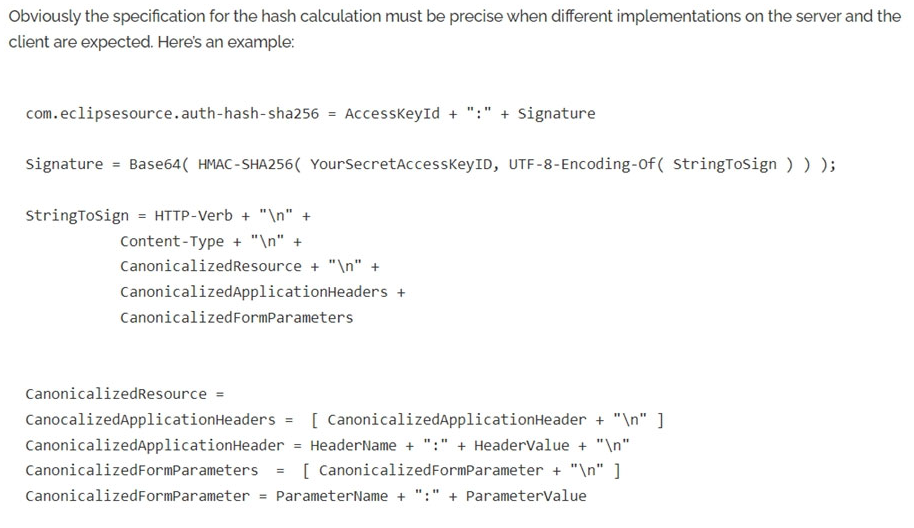
| Question.48 A security engineer was auditing an organization’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops. Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries? (A) Perform additional SAST/DAST on the open-source libraries. (B) Implement the SDLC security guidelines. (C) Track the library versions and monitor the CVE website for related vulnerabilities. (D) Perform unit testing of the open-source libraries. |
48. Click here to View Answer
Answer: C
| Question.49 A company invested a total of $10 million for a new storage solution installed across five on-site datacenters. Fifty percent of the cost of this investment was for solid-state storage. Due to the high rate of wear on this storage, the company is estimating that 5% will need to be replaced per year. Which of the following is the ALE due to storage replacement? (A) $50,000 (B) $125,000 (C) $250,000 (D) $500,000 (E) $1,000,000 |
49. Click here to View Answer
Answer: C
| Question.50 During an incident, an employee’s web traffic was redirected to a malicious domain. The workstation was compromised, and the attacker was able to modify sensitive data from the company file server. Which of the following solutions would have BEST prevented the initial compromise from happening? (Choose two.) (A) DNSSEC (B) FIM (C) Segmentation (D) Firewall (E) DLP (F) Web proxy |
50. Click here to View Answer
Answer: AF
