| Question.11 A pharmaceutical company was recently compromised by ransomware. Given the following EDR output from the process investigation: 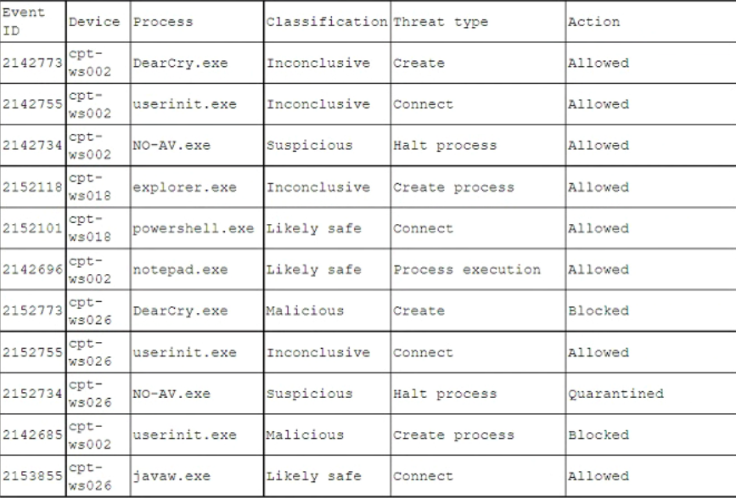 On which of the following devices and processes did the ransomware originate? (A) cpt-ws018, powershell.exe (B) cpt-ws026, DearCry.exe (C) cpt-ws002, NO-AV.exe (D) cpt-ws026, NO-AV.exe (E) cpt-ws002, DearCry.exe |
11. Click here to View Answer
Answer: C
| Question.12 A security architect is reviewing the following proposed corporate firewall architecture and configuration: 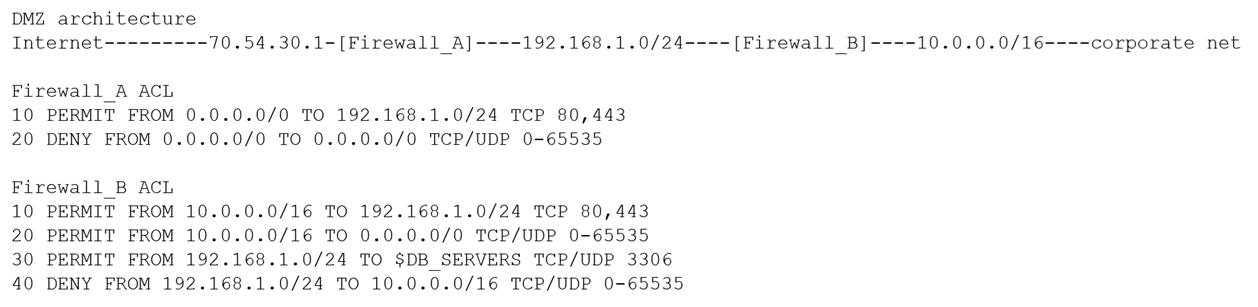 Both firewalls are stateful and provide Layer 7 filtering and routing. The company has the following requirements: Web servers must receive all updates via HTTP/S from the corporate network. Web servers should not initiate communication with the Internet. Web servers should only connect to preapproved corporate database servers. Employees’ computing devices should only connect to web services over ports 80 and 443. Which of the following should the architect recommend to ensure all requirements are met in the MOST secure manner? (Choose two.) (A) Add the following to Firewall_A: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0/0 TCP 80,443 (B) Add the following to Firewall_A: 15 PERMIT FROM 192.168.1.0/24 TO 0.0.0.0 TCP 80,443 (C) Add the following to Firewall_A: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0/0 TCP/UDP 0-65535 (D) Add the following to Firewall_B: 15 PERMIT FROM 0.0.0.0/0 TO 10.0.0.0/16 TCP/UDP 0-65535 (E) Add the following to Firewall_B: 15 PERMIT FROM 10.0.0.0/16 TO 0.0.0.0 TCP/UDP 0-65535 (F) Add the following to Firewall_B: 15 PERMIT FROM 192.168.1.0/24 TO 10.0.2.10/32 TCP 80,443 Show Answer |
12. Click here to View Answer
Answer: BD
| Question.13 A third-party organization has implemented a system that allows it to analyze customers data and deliver analysis results without being able to see the raw data. Which of the following is the organization implementing? (A) Asynchronous keys (B) Homomorphic encryption (C) Data lake (D) Machine learning |
13. Click here to View Answer
Answer: B
| Question.14 An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft. Which of the following can be used to mitigate this risk? (A) An additional layer of encryption (B) A third-party, data integrity monitoring solution (C) A complete backup that is created before moving the data (D) Additional application firewall rules specific to the migration |
14. Click here to View Answer
Answer: A
| Question.15 A security analyst is evaluating the security of an online customer banking system. The analyst has a 12-character password for the test account. At the login screen, the analyst is asked to enter the third, eighth, and eleventh characters of the password. Which of the following describes why this request is a security concern? (Choose two.) (A) The request is evidence that the password is more open to being captured via a keylogger. (B) The request proves that salt has not been added to the password hash, thus making it vulnerable to rainbow tables. (C) The request proves the password is encoded rather than encrypted and thus less secure as it can be easily reversed. (D) The request proves a potential attacker only needs to be able to guess or brute force three characters rather than 12 characters of the password. (E) The request proves the password is stored in a reversible format, making it readable by anyone at the bank who is given access. (F) The request proves the password must be in cleartext during transit, making it open to on-path attacks. |
15. Click here to View Answer
Answer: DE
