| Question.36 A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:  The security engineer looks at the UTM firewall rules and finds the following: 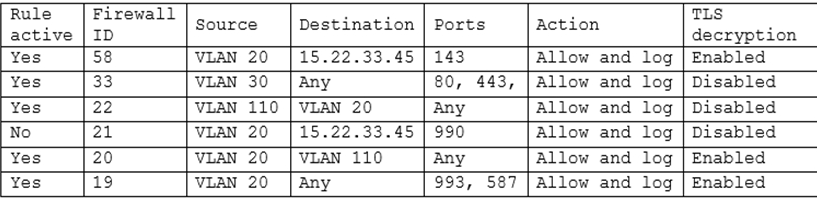 Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network? (A) Contact the email service provider and ask if the company IP is blocked. (B) Confirm the email server certificate is installed on the corporate computers. (C) Make sure the UTM certificate is imported on the corporate computers. (D) Create an IMAPS firewall rule to ensure email is allowed. |
36. Click here to View Answer
Answer: B
| Question.37 An application server was recently upgraded to prefer TLS 1.3, and now users are unable to connect their clients to the server. Attempts to reproduce the error are confirmed, and clients are reporting the following: ERR_SSL_VERSION_OR_CIPHER_MISMATCH Which of the following is MOST likely the root cause? (A) The client application is testing PFS. (B) The client application is configured to use ECDHE. (C) The client application is configured to use RC4. (D) The client application is configured to use AES-256 in GCM. |
37. Click here to View Answer
Answer: C
| Question.38 A healthcare system recently suffered from a ransomware incident. As a result, the board of directors decided to hire a security consultant to improve existing network security. The security consultant found that the healthcare network was completely flat, had no privileged access limits, and had open RDP access to servers with personal health information. As the consultant builds the remediation plan, which of the following solutions would BEST solve these challenges? (Choose three.) (A) SD-WAN (B) PAM (C) Remote access VPN (D) MFA (E) Network segmentation (F) BGP (G) NAC |
38. Click here to View Answer
Answer: CDG
| Question.39 A security consultant is designing an infrastructure security solution for a client company that has provided the following requirements: Access to critical web services at the edge must be redundant and highly available. Secure access services must be resilient to a proprietary zero-day vulnerability in a single component. Automated transition of secure access solutions must be able to be triggered by defined events or manually by security operations staff. Which of the following solutions BEST meets these requirements? (A) Implementation of multiple IPSec VPN solutions with diverse endpoint configurations enabling user optionality in the selection of a remote access provider. (B) Remote access services deployed using vendor-diverse redundancy with event response driven by playbooks. (C) Two separate secure access solutions orchestrated by SOAR with components provided by the same vendor for compatibility. (D) Reverse TLS proxy configuration using OpenVPN/OpenSSL with scripted failover functionality that connects critical web services out to endpoint computers. |
39. Click here to View Answer
Answer: B
| Question.40 A forensic investigator would use the foremost command for: (A) cloning disks. (B) analyzing network-captured packets. (C) recovering lost files. (D) extracting features such as email addresses. |
40. Click here to View Answer
Answer: C
