| Question.41 A systems administrator confirms that the company’s remote server is providing the following list of preferred ciphers: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) TLS_RSA_WITH_RC4_128_SHA (0x5) TLS_RSA_WITH_RC4_128_MD5 (0x4) Nevertheless, when the systems administrator’s browser connects to the server, it negotiates TLS_RSA_WITH_RC4_128_MD5 (0x4), while all other employees’ browsers negotiate TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030). Which of the following describes a potential attack to the systems administrator’s browser? (A) A cipher mismatch (B) Key rotation (C) A downgrade attack (D) A compromised key (E) Rekeying |
41. Click here to View Answer
Answer: C
| Question.42 Users are claiming that a web server is not accessible. A security engineer is unable to view the Internet Services logs for the site. The engineer connects to the server and runs netstat an and receives the following output:  Which of the following is MOST likely happening to the server? (A) Port scanning (B) ARP spoofing (C) Buffer overflow (D) Denial of service |
42. Click here to View Answer
Answer: D
| Question.43 Which of the following represents the MOST significant benefit of implementing a passwordless authentication solution? (A) Biometric authenticators are immutable. (B) The likelihood of account compromise is reduced. (C) Zero trust is achieved. (D) Privacy risks are minimized. |
43. Click here to View Answer
Answer: B
| Question.44 A client is adding scope to a project. Which of the following processes should be used when requesting updates or corrections to the client’s systems? (A) The implementation engineer requests direct approval from the systems engineer and the Chief Information Security Officer. (B) The change control board must review and approve a submission. (C) The information system security officer provides the systems engineer with the system updates. (D) The security engineer asks the project manager to review the updates for the client’s system. |
44. Click here to View Answer
Answer: B
| Question.45 An auditor is reviewing the logs from a web application to determine the source of an incident. The web application architecture includes an Internet-accessible application load balancer, a number of web servers in a private subnet, application servers, and one database server in a tiered configuration. The application load balancer cannot store the logs. The following are sample log snippets: 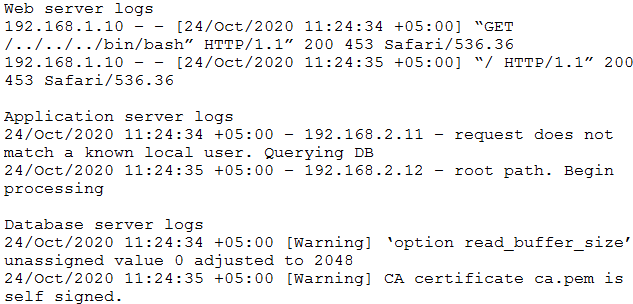 Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources? (A) Enable the X-Forwarded-For header at the load balancer. (B) Install a software-based HIDS on the application servers. (C) Install a certificate signed by a trusted CA. (D) Use stored procedures on the database server. (E) Store the value of the $_SERVER[‘REMOTE_ADDR’] received by the web servers. |
45. Click here to View Answer
Answer: C
