| Question.11 You have an Azure subscription. The subscription contains Azure virtual machines that run Windows Server 2016 and Linux. You need to use Azure Monitor to design an alerting strategy for security-related events. Which Azure Monitor Logs tables should you query? In the real exam, drag the appropriate tables to the correct log types. Each table may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. Each correct selection is worth one point. Select and Place: 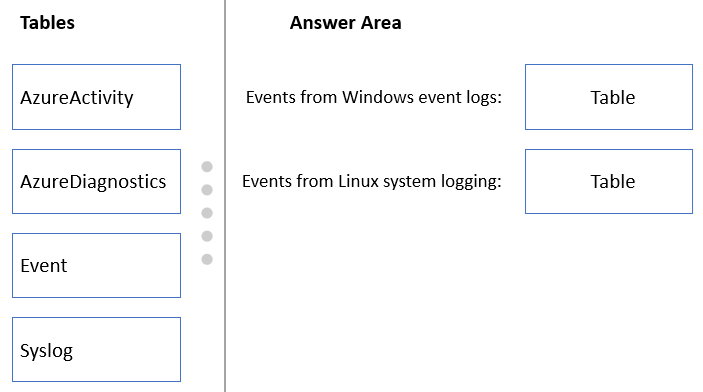 Check the answer section Check the answer section |
11. Click here to View Answer
To design an alerting strategy for security-related events in Azure Monitor, you should query the following Azure Monitor Logs tables:
1. SecurityEvent – This table contains security events and other system events that are generated by Windows operating systems. The table includes information about the event, such as the event ID, event source, and severity level.
2. Syslog – This table contains security-related events and other system events that are generated by Linux and other Unix-based operating systems. The table includes information about the event, such as the facility and severity level.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/data-sources-windows-events
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-syslog
| Question.12 DRAG DROP – Your on-premises network contains a server named Server1 that runs an ASP.NET application named App1. You have a hybrid deployment of Azure Active Directory (Azure AD). You need to recommend a solution to ensure that users sign in by using their Azure AD account and Azure Multi-Factor Authentication (MFA) when they connect to App1 from the internet. Which three features should you recommend be deployed and configured in sequence? To answer, move the appropriate features from the list of features to the answer area and arrange them in the correct order. Select and Place:  |
12. Click here to View Answer
Answer:

Explanation:
Step 1: Azure AD Application Proxy.
Start by enabling communication to Azure data centers to prepare your environment for Azure AD Application Proxy.
Step 2: an Azure AD enterprise application.
Represents an application integrated with Azure AD for identity and access management.
Step 3: A Conditional Access Policy.
Enforces access controls like multi-factor authentication (MFA) based on user conditions.
Reference:
| Question.13 You need to recommend a solution to generate a monthly report of all the new Azure Resource Manager (ARM) resource deployments in your Azure subscription. What should you include in the recommendation? (A) Azure Activity Log (B) Azure Advisor (C) Azure Analysis Services (D) Azure Monitor action groups |
13. Click here to View Answer
Answer: A
Explanation:
Activity logs are kept for 90 days. You can query for any range of dates, as long as the starting date isn’t more than 90 days in the past.
Through activity logs, you can determine:
✑ what operations were taken on the resources in your subscription
✑ who started the operation
✑ when the operation occurred
✑ the status of the operation
✑ the values of other properties that might help you research the operation
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/view-activity-logs
| Question.14 Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company deploys several virtual machines on-premises and to Azure. ExpressRoute is deployed and configured for on-premises to Azure connectivity. Several virtual machines exhibit network connectivity issues. You need to analyze the network traffic to identify whether packets are being allowed or denied to the virtual machines. Solution: Install and configure the Azure Monitoring agent and the Dependency Agent on all the virtual machines. Use VM insights in Azure Monitor to analyze the network traffic. Does this meet the goal? (A) Yes (B) No |
14. Click here to View Answer
Answer: B
Explanation:
Use the Azure Monitor agent if you need to:
Collect guest logs and metrics from any machine in Azure, in other clouds, or on-premises.
Use the Dependency agent if you need to:
Use the Map feature VM insights or the Service Map solution.
Note: Instead use Azure Network Watcher IP Flow Verify allows you to detect traffic filtering issues at a VM level.
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen,
IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview#dependency-agent
| Question.15 DRAG DROP – You need to design an architecture to capture the creation of users and the assignment of roles. The captured data must be stored in Azure Cosmos DB. Which services should you include in the design? To answer, drag the appropriate services to the correct targets. Each service may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place: 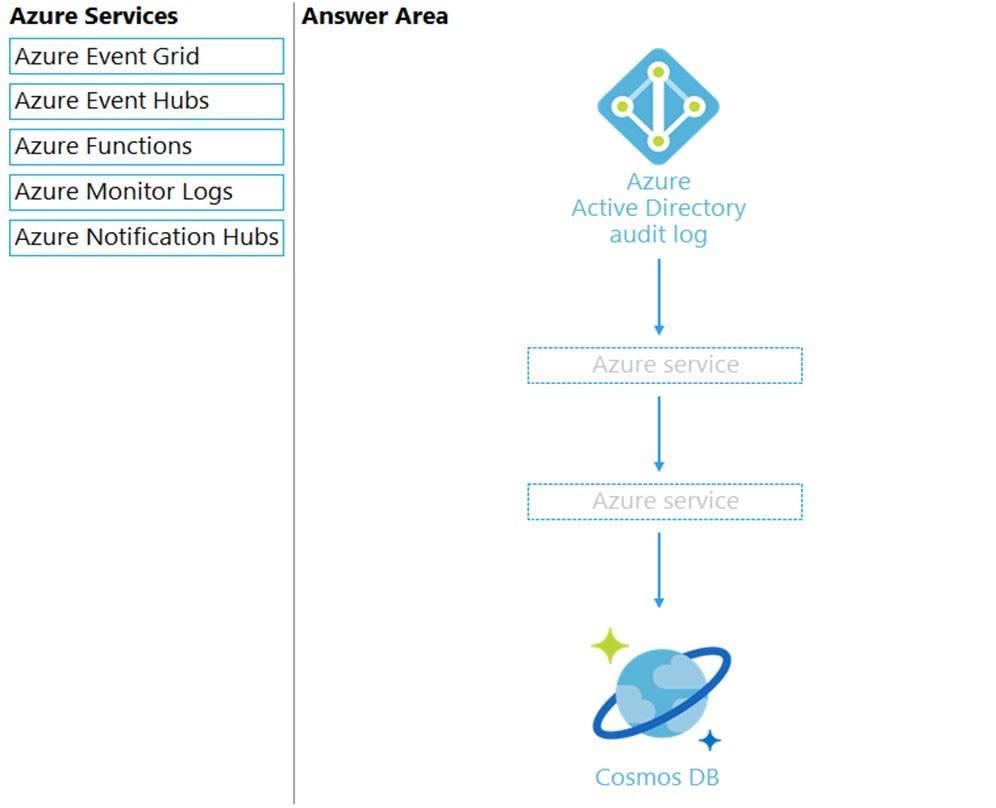 |
15. Click here to View Answer
Answer:

Explanation:
Box 1: Azure Event Hubs –
You can route Azure Active Directory (Azure AD) activity logs to several endpoints for long term retention and data insights.
The Event Hub is used for streaming.
Box 2: Azure Function –
Use an Azure Function along with a cosmos DB change feed, and store the data in Cosmos DB.
