| Question.31 A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that is integrated with Microsoft 365 and an Azure subscription. Contoso has an on-premises identity infrastructure. The infrastructure includes servers that run Active Directory Domain Services (AD DS) and Azure AD Connect. Contoso has a partnership with a company named Fabrikam. Inc. Fabrikam has an Active Directory forest and a Microsoft 365 tenant. Fabrikam has the same on- premises identity infrastructure components as Contoso. A team of 10 developers from Fabrikam will work on an Azure solution that will be hosted in the Azure subscription of Contoso. The developers must be added to the Contributor role for a resource group in the Contoso subscription. You need to recommend a solution to ensure that Contoso can assign the role to the 10 Fabrikam developers. The solution must ensure that the Fabrikam developers use their existing credentials to access resources What should you recommend? (A) In the Azure AD tenant of Contoso. create cloud-only user accounts for the Fabrikam developers. (B) Configure a forest trust between the on-premises Active Directory forests of Contoso and Fabrikam. (C) Configure an organization relationship between the Microsoft 365 tenants of Fabrikam and Contoso. (D) In the Azure AD tenant of Contoso, create guest accounts for the Fabnkam developers. |
31. Click here to View Answer
Answer: D
Explanation:
You can use the capabilities in Azure Active Directory B2B to collaborate with external guest users and you can use Azure RBAC to grant just the permissions that guest users need in your environment.
Incorrect:
Not B: Forest trust is used for internal security, not external access.
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-external-users
| Question.32 Your company has the divisions shown in the following table.  Sub1 contains an Azure App Service web app named App1. App1 uses Azure AD for single-tenant user authentication. Users from contoso.com can authenticate to App1. You need to recommend a solution to enable users in the fabrikam.com tenant to authenticate to App1. What should you recommend? (A) Configure the Azure AD provisioning service. (B) Enable Azure AD pass-through authentication and update the sign-in endpoint. (C) Use Azure AD entitlement management to govern external users. (D) Configure Azure AD join. |
32. Click here to View Answer
Answer: C
Explanation:
The app is single tenant authentication so users must be present in contoso directory.
With Azure AD B2B, external users authenticate to their home directory, but have a representation in your directory.
A is wrong because its to automate provisioning to third party SaaS app.
B. is wrong because the application would need to switch to multi tenant..
https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-convert-app-to-be-multi-tenant
| Question.33 HOTSPOT – Your company has 20 web APIs that were developed in-house. The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management. You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs. The solution must meet the following requirements: ✑ Use Azure AD-generated claims. Minimize configuration and management effort.  What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:  |
33. Click here to View Answer
Answer:
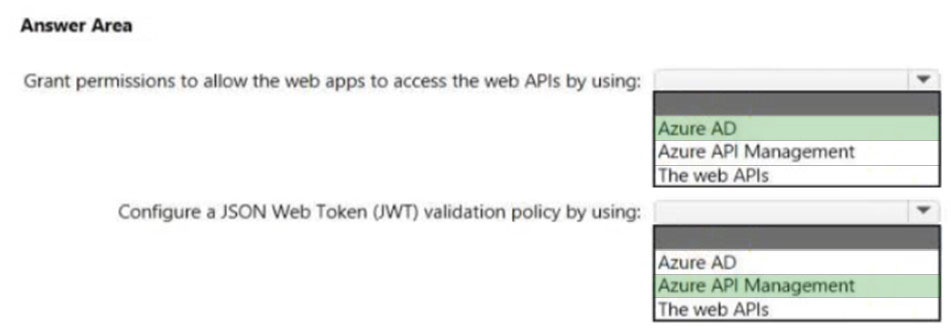
Explanation:
Box 1: Azure AD –
Grant permissions in Azure AD.
Box 2: Azure API Management –
Configure a JWT validation policy to pre-authorize requests.
Pre-authorize requests in API Management with the Validate JWT policy, by validating the access tokens of each incoming request. If a request does not have a valid token, API Management blocks it.
Reference:
https://docs.microsoft.com/en-us/azure/api-management/api-management-howto-protect-backend-with-aad
| Question.34 You need to recommend a solution to generate a monthly report of all the new Azure Resource Manager (ARM) resource deployments in your Azure subscription. What should you include in the recommendation? (A) Azure Log Analytics (B) Azure Arc (C) Azure Analysis Services (D) Application Insights |
34. Click here to View Answer
Answer: A
Explanation:
The Activity log is a platform log in Azure that provides insight into subscription-level events. Activity log includes such information as when a resource is modified or when a virtual machine is started.
Activity log events are retained in Azure for 90 days and then deleted.
For more functionality, you should create a diagnostic setting to send the Activity log to one or more of these locations for the following reasons: to Azure Monitor Logs for more complex querying and alerting, and longer retention (up to two years) to Azure Event Hubs to forward outside of Azure to Azure Storage for cheaper, long-term archiving
Note: Azure Monitor builds on top of Log Analytics, the platform service that gathers log and metrics data from all your resources. The easiest way to think about it is that Azure Monitor is the marketing name, whereas Log Analytics is the technology that powers it.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/essentials/activity-log
| Question.35 Your company has the divisions shown in the following table.  Sub1 contains an Azure App Service web app named App1. App1 uses Azure AD for single-tenant user authentication. Users from contoso.com can authenticate to App1. You need to recommend a solution to enable users in the fabrikam.com tenant to authenticate to App1. What should you recommend? (A) Configure the Azure AD provisioning service. (B) Configure assignments for the fabrikam.com users by using Azure AD Privileged Identity Management (PIM). (C) Use Azure AD entitlement management to govern external users. (D) Configure Azure AD Identity Protection. |
35. Click here to View Answer
Answer: C
Explanation:
Entitlement management is an identity governance capability that enables organizations to manage identity and access lifecycle at scale by automating access request workflows, access assignments, reviews, and expiration. Entitlement management allows delegated non-admins to create access packages that external users from other organizations can request access to. One and multi-stage approval workflows can be configured to evaluate requests, and provision users for time-limited access with recurring reviews. Entitlement management enables policy-based provisioning and deprovisioning of external accounts.
Note: Access Packages –
An access package is the foundation of entitlement management. Access packages are groupings of policy-governed resources a user needs to collaborate on a project or do other tasks. For example, an access package might include: access to specific SharePoint sites. enterprise applications including your custom in-house and SaaS apps like Salesforce.
Microsoft Teams.
Microsoft 365 Groups.
Incorrect:
Not A: Automatic provisioning refers to creating user identities and roles in the cloud applications that users need access to. In addition to creating user identities, automatic provisioning includes the maintenance and removal of user identities as status or roles change.
Not B: Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Etc.
