| Question.46 You have an Azure Data Factory version 2 (V2) resource named Df1. Df1 contains a linked service. You have an Azure Key vault named vault1 that contains an encryption key named key1. You need to encrypt Df1 by using key1. What should you do first? A. Add a private endpoint connection to vault1. B. Enable Azure role-based access control on vault1. C. Remove the linked service from Df1. D. Create a self-hosted integration runtime. |
46. Click here to View Answer
Answer:
C
Explanation:
Linked services are much like connection strings, which define the connection information needed for Data Factory to
connect to external resources.
Incorrect Answers:
D: A self-hosted integration runtime copies data between an on-premises store and cloud storage.
Reference: https://docs.microsoft.com/en-us/azure/data-factory/enable-customer-managed-key
https://docs.microsoft.com/en-us/azure/data-factory/concepts-linked-services https://docs.microsoft.com/en-us/azure/data-
factory/create-self-hosted-integration-runtime
| Question.47 You develop data engineering solutions for a company. A project requires the deployment of data to Azure Data Lake Storage. You need to implement role-based access control (RBAC) so that project members can manage the Azure Data Lake Storage resources. Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Create security groups in Azure Active Directory (Azure AD) and add project members. B. Configure end-user authentication for the Azure Data Lake Storage account. C. Assign Azure AD security groups to Azure Data Lake Storage. D. Configure Service-to-service authentication for the Azure Data Lake Storage account. E. Configure access control lists (ACL) for the Azure Data Lake Storage account. |
47. Click here to View Answer
Answer:
A C E
Explanation:
AC: Create security groups in Azure Active Directory. Assign users or security groups to Data Lake Storage Gen1 accounts.
E: Assign users or security groups as ACLs to the Data Lake Storage Gen1 file system
Reference: https://docs.microsoft.com/en-us/azure/data-lake-store/data-lake-store-secure-data
| Question.48 You are designing an enterprise data warehouse in Azure Synapse Analytics that will contain a table named Customers. Customers will contain credit card information. You need to recommend a solution to provide salespeople with the ability to view all the entries in Customers. The solution must prevent all the salespeople from viewing or inferring the credit card information. What should you include in the recommendation? A. data masking B. Always Encrypted C. column-level security D. row-level security |
48. Click here to View Answer
Answer:
C
Explanation:
Column-level security simplifies the design and coding of security in your application, allowing you to restrict column access
to protect sensitive data.
Reference: https://docs.microsoft.com/en-us/azure/synapse-analytics/sql-data-warehouse/column-level-security
| Question.49 You plan to create an Azure Synapse Analytics dedicated SQL pool. You need to minimize the time it takes to identify queries that return confidential information as defined by the company’s data privacy regulations and the users who executed the queues. Which two components should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. sensitivity-classification labels applied to columns that contain confidential information B. resource tags for databases that contain confidential information C. audit logs sent to a Log Analytics workspace D. dynamic data masking for columns that contain confidential information |
49. Click here to View Answer
Answer:
A C
Explanation:
A: You can classify columns manually, as an alternative or in addition to the recommendation-based classification: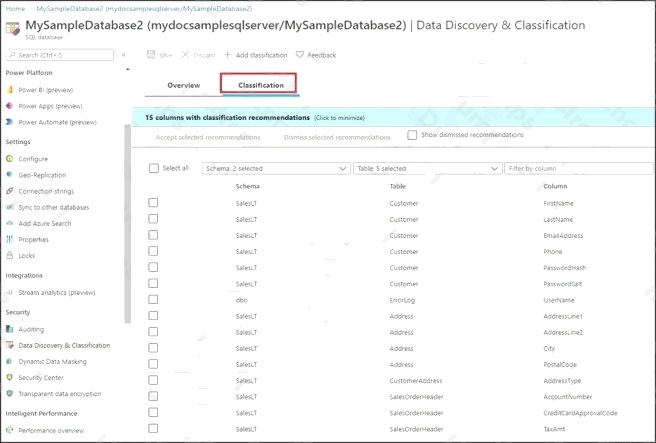
1. Select Add classification in the top menu of the pane.
2. In the context window that opens, select the schema, table, and column that you want to classify, and the information type
and sensitivity label.
3. Select Add classification at the bottom of the context window.
C: An important aspect of the information-protection paradigm is the ability to monitor access to sensitive data. Azure SQL
Auditing has been enhanced to include a new field in the audit log called data_sensitivity_information. This field logs the
sensitivity classifications (labels) of the data that was returned by a query. Here’s an example: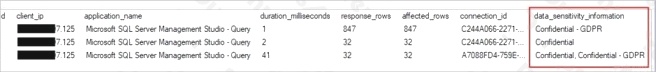
Reference: https://docs.microsoft.com/en-us/azure/azure-sql/database/data-discovery-and-classification-overview
| Question.50 HOTSPOT You have an Azure subscription that contains a logical Microsoft SQL server named Server1. Server1 hosts an Azure Synapse Analytics SQL dedicated pool named Pool1. You need to recommend a Transparent Data Encryption (TDE) solution for Server1. The solution must meet the following requirements: Track the usage of encryption keys.  Maintain the access of client apps to Pool1 in the event of an Azure datacenter outage that affects the availability of the  encryption keys. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area: 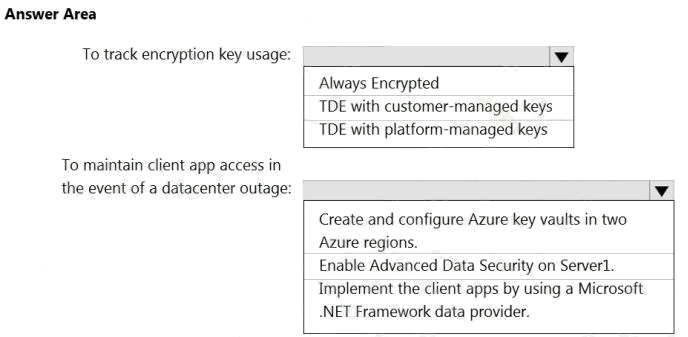 |
50. Click here to View Answer
Answer:
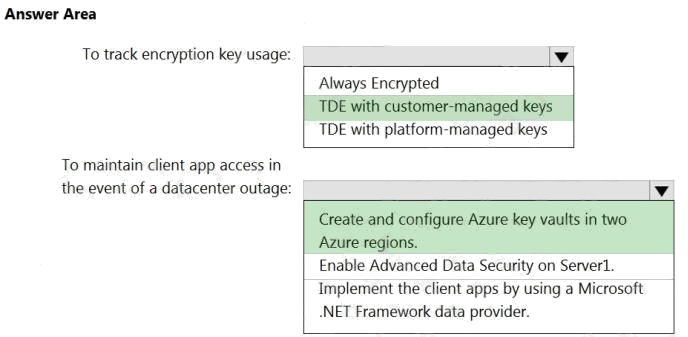
Explanation:
Box 1: TDE with customer-managed keys
Customer-managed keys are stored in the Azure Key Vault. You can monitor how and when your key vaults are accessed,
and by whom. You can do this by enabling logging for Azure Key Vault, which saves information in an Azure storage account
that you provide.
Box 2: Create and configure Azure key vaults in two Azure regions
The contents of your key vault are replicated within the region and to a secondary region at least 150 miles away, but within
the same geography to maintain high durability of your keys and secrets.
Reference:
https://docs.microsoft.com/en-us/azure/synapse-analytics/security/workspaces-encryption https://docs.microsoft.com/en-
us/azure/key-vault/general/logging
